Configure SAML assertion attributes
SAML attributes are key components of SAML assertions that carry specific information about the authenticated user. These attributes can include user identifiers, roles, permissions, and other relevant user data that the Service Provider (SP) may need for authorization and personalization purposes.
Understanding SAML attributes
In SAML authentication:
- Attributes are name-value pairs that contain user information
- They are included in the SAML assertion sent from the Identity Provider (Logto) to the Service Provider
- They help Service Providers make informed decisions about user access and personalization
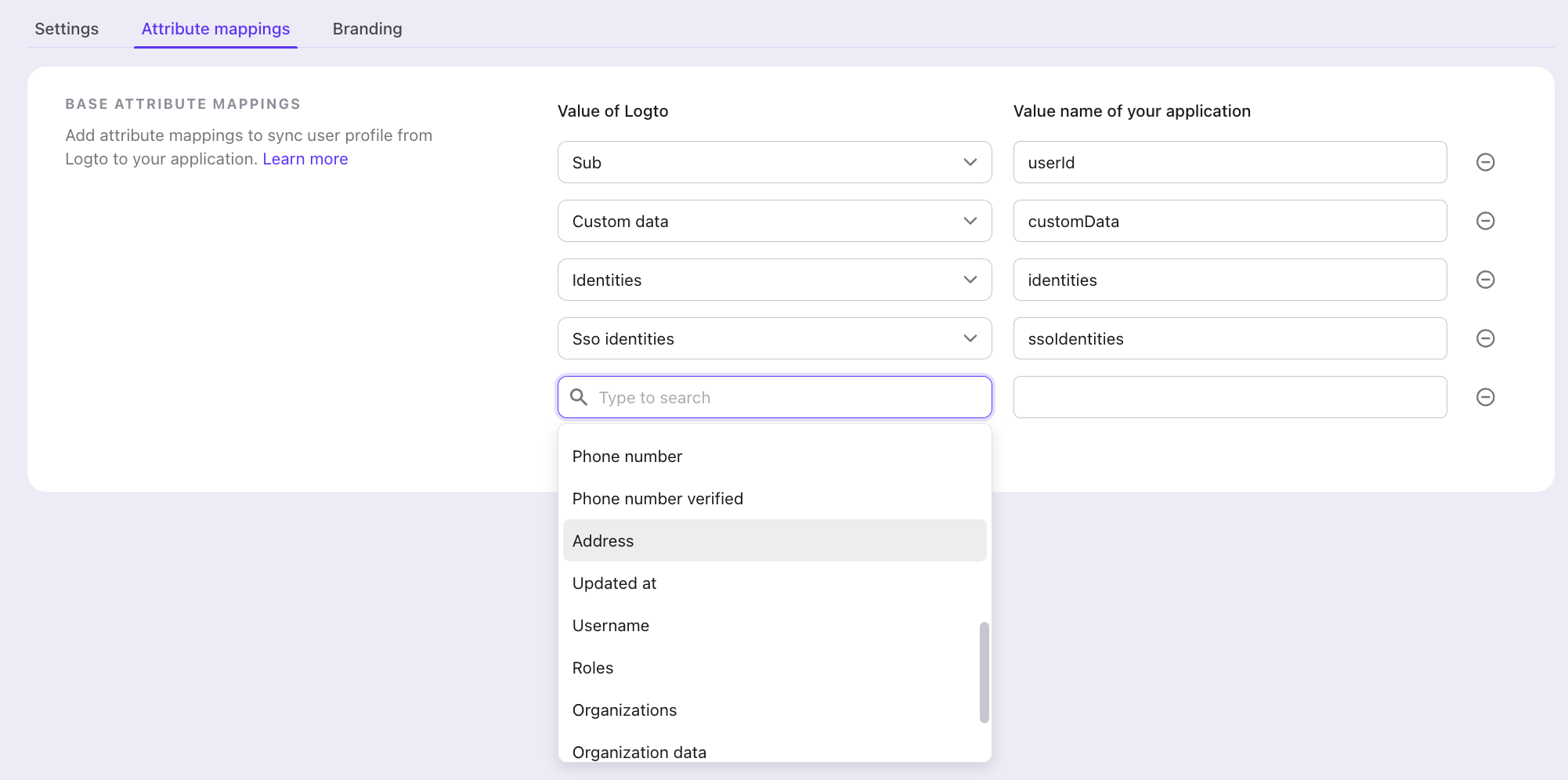
Attribute mapping in Logto
Attribute mapping allows you to define how user information from Logto should be mapped to specific attributes in the SAML assertion. This mapping ensures that your Service Provider receives the user information in the expected format and under the expected attribute names.
When you configure attribute mapping:
- You specify which user properties from Logto should be included in the SAML assertion
- You define custom attribute names that your Service Provider expects
- The mapped attributes are automatically included in the SAML assertion during authentication
Common attributes
Some commonly used SAML attributes include:
- Sub (User ID)
- Organizations
- Name
- Preferred username
View all user data available from Logto
By properly configuring attribute mapping, you ensure that your Service Provider receives all the necessary user information to provide appropriate access and personalization for your users.
You can map all Logto available user information to your SP's expected attributes using the attribute mapping settings.