Configure MFA
Configure MFA settings in Logto
Logto provides flexible MFA configuration options to meet different security requirements. You can configure MFA at the global level for all users or enable it on a per-organization basis for multi-tenant applications.
Global MFA configuration
Follow these steps to enable MFAs in users' Logto sign-in flow:
- Navigate to: Console > Multi-factor auth.
- Enable the supported verification factors for your users.
- Primary factors:
- Passkeys (WebAuthn): A high-security option suitable for web products supporting device biometrics or security keys, etc., ensuring robust protection.
- Authenticator App OTP: The most common and widely accepted method. Use a time-based one-time password (TOTP) generated by an authenticator app like Google Authenticator or Authy.
- SMS verification: A convenient method that sends one-time verification codes via SMS to the user's registered phone number, ideal for users who prefer mobile-based authentication without additional apps.
- Email verification: A widely accessible method that delivers one-time verification codes to the user's registered email address, suitable for users across all platforms and devices.
- Backup factors:
- Backup codes: This serves as a backup option when users can't verify any of the primary factors mentioned above. Enabling this option reduces friction for users' access successfully.
- Primary factors:
- Choose if you want to enable Require MFA:
- Enable: Users will be prompted to set up MFA during the sign-in process which cannot be skipped. If the user fails to set up MFA or deletes their MFA settings, they will be locked out of their account until they set up MFA again.
- Disable: Users can skip the MFA setup process during the sign-up flow. They may set up MFA later through your self-service account settings page. Learn more about implementing a user account settings page. And continue to choose the policy for the MFA setup prompt:
- Do not ask users to set up MFA: Users will not be prompted to set up MFA during sign-in.
- Ask users to set up MFA during registration: New users will be prompted to set up MFA during registration, and existing users will see the prompt at their next sign-in. Users can skip this step, and it won't appear again.
- Ask users to set up MFA on their sign-in after registration: New users will be prompted to set up MFA at their second sign-in after registration, and existing users will see the prompt at their next sign-in. Users can skip this step, and it won't appear again.
If you need to prompt a user again after they skipped MFA enrollment, reset their skip state so the setup screen appears the next time they sign in. Admins can use the Management API (PATCH /api/users/{userId}/logto-configs), and developers building self-service flows can call the Account API (PATCH /api/my-account/logto-configs). Management API reference · Account API reference
Organization-level MFA configuration
For products with a multi-tenant architecture that support Organizations, in most cases you don't need to require MFA for all users. Instead, MFA can be enabled on a per-organization basis, allowing you to tailor the requirements based on each client's needs. To get started, refer to Requiring MFA for organization members.
In the Multi-factor authentication section, set MFA setup prompt for users after organization enables MFA to Ask users to set up MFA on next sign-in (no skipping). Members of any organization that requires MFA will then be prompted to complete MFA setup at their next sign-in, and the prompt cannot be skipped.
MFA user flow
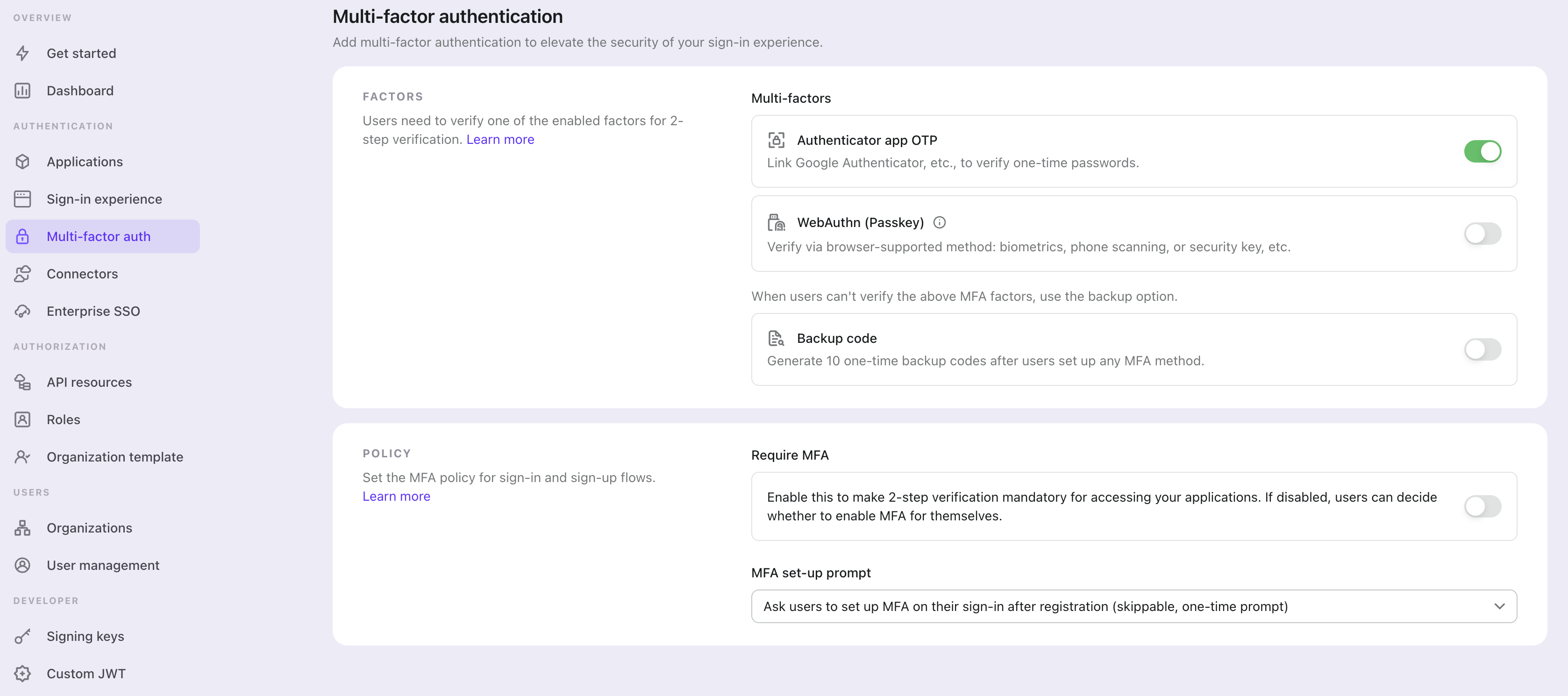
MFA set-up flow
Once the MFA is enabled, users will be prompted to set up MFA during the sign-in and sign-up process. Users can choose to skip this setup process if and only if the “Require MFA“ policy is disabled.
- Visit sign-in or sign-up page: The user navigates to the sign-in or sign-up page.
- Completes sign-in or sign-up: The user completes the identity verification process within the sign-in or sign-up flow.
- Set up MFA primary factor: The user is prompted to set up their primary MFA factor (either passkey, Authenticator app OTP, SMS code, or email code).
- If multiple primary factors are enabled, they can choose their preferred option.
- If the primary factor is the same as the sign-up identifier (e.g., SMS or email), it will be pre-verified, allowing users to skip the verification step and proceed directly to the next step (e.g., "Add another one 2-step verification" or "Save your backup factors").
- If the “Require MFA” policy is disabled, they can also skip this step by selecting the "Skip" button.
- Set up MFA backup factor: If Backup codes are enabled, the user is prompted to save backup codes after successfully configuring their primary authentication factor. Auto generated backup codes will be displayed to the user, which they can download and store securely. User must manually confirm the backup codes to complete the MFA setup process.
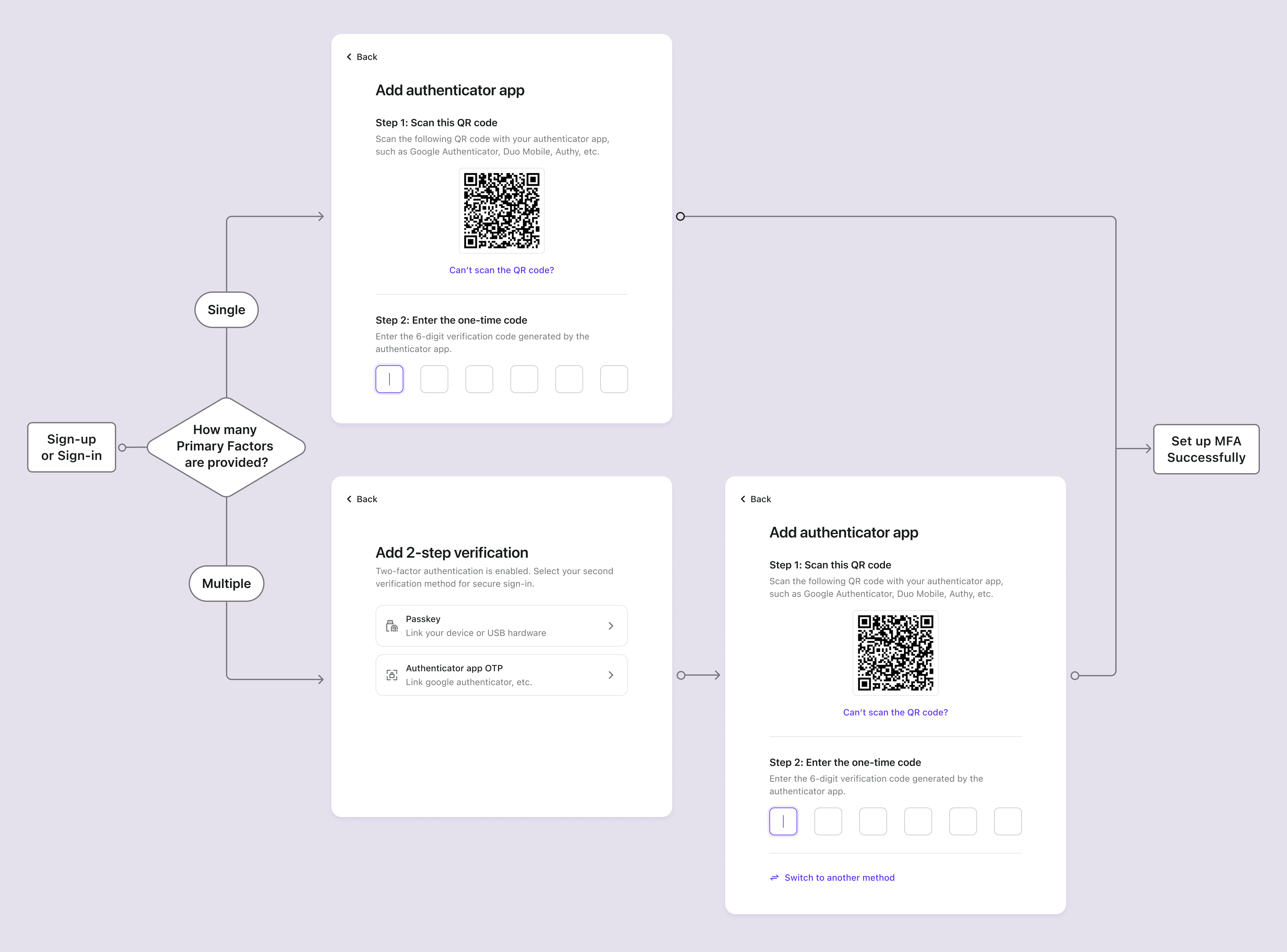
MFA verification flow
Users who have set up MFA will be prompted to verify their identity using their configured MFA factors during sign-in. The verification factor will depend on the MFA configuration in Logto and the user settings.
- If a user has set up only one factor, they will verify it directly.
- If a user has set up multiple factors for 2FA, the system will present verification options based on the following priority rules:
- Passkey priority: If the user has a passkey configured, it will be presented as the default verification method.
- Last-used preference: If no passkey is available, the system will prioritize the verification method the user last successfully used.
- Selection list: If neither of the above priorities apply, the 2-step verification page will display all available bound verification methods for the user to choose from.
- Users can click "Try another method to verify" to switch between different verification options at any time.
- If all the enabled primary factors are not available to the user, and backup code is enabled, they can use the one-time backup code to verify their identity.
MFA management
Beyond the initial setup during sign-in/sign-up, users can manage their MFA settings through a self-service account center. This provides flexibility for users to bind or unbind MFA factors based on their needs.
Building an account center
You can build a comprehensive account center using Logto's Account API, which allows users to:
- Bind new MFA factors: Add additional authenticator apps, passkeys, or regenerate backup codes
- Unbind existing MFA factors: Remove MFA methods they no longer wish to use
- View current MFA status: See which MFA factors are currently configured
Post-login MFA setup prompts
For applications that don't require MFA during initial registration, you can implement intelligent prompts to encourage MFA setup:
- Conditional prompts: Show MFA setup recommendations based on user behavior or account value
- Security dashboards: Display security scores that improve when MFA is enabled
- Gradual onboarding: Present MFA setup as part of a progressive security enhancement flow
Learn more about implementing these patterns with Account API.
Manage user's MFA in Console
In the Console > User management, administrators can manage user MFA settings effectively:
- View user MFA status: Check which MFA factors are enabled for each user.
- Remove user MFA: Delete all MFA factors for a user, requiring them to set up MFA again.
FAQs
What happens when administrators remove user's existing MFA factors?
When administrators remove all of a user's primary MFA factors (passkey, authenticator app OTP, SMS, or email), the following scenarios will occur during the user's next sign-in:
Scenario 1: No MFA factors remain
- If no MFA factors exist (including no backup codes) and the MFA policy requires MFA, the user will be allowed to sign in without MFA verification and will be immediately prompted to set up MFA again.
Scenario 2: Backup codes still exist
- If backup codes are still available, the user must first verify using a backup code during sign-in.
- After successful backup code verification, the user will be prompted to set up a new primary MFA factor.
- Whether the user can skip this setup depends on your configured MFA policy.
- This approach prevents users from being locked out of their accounts when no primary factors are available.