Permission management of the OIDC / OAuth application
Third-party applications, not owned by your service, are integrated with Logto as identity providers to authenticate users. These apps, typically from external service providers, require careful permission management to protect user data.
Logto empowers you to control the specific permissions granted to third-party applications. This includes managing user profile, API resource, and organization scopes. Unlike first-party apps, third-party apps requesting unauthorized scopes will be denied access.
By enabling specific scopes, you determine which user information third-party apps can access. Users will review and approve these permissions on the consent screen before granting access.
Manage the permissions of your OIDC third-party applications
Go to the Console > Applications > Application details page of your OIDC third-party application and navigate to the Permissions tab and click on the Add permissions button to manage the permissions of your third-party applications.
Basic user data is always required for third-party app requests. Additionally, Logto supports assigning organization resources, making it ideal for B2B services.
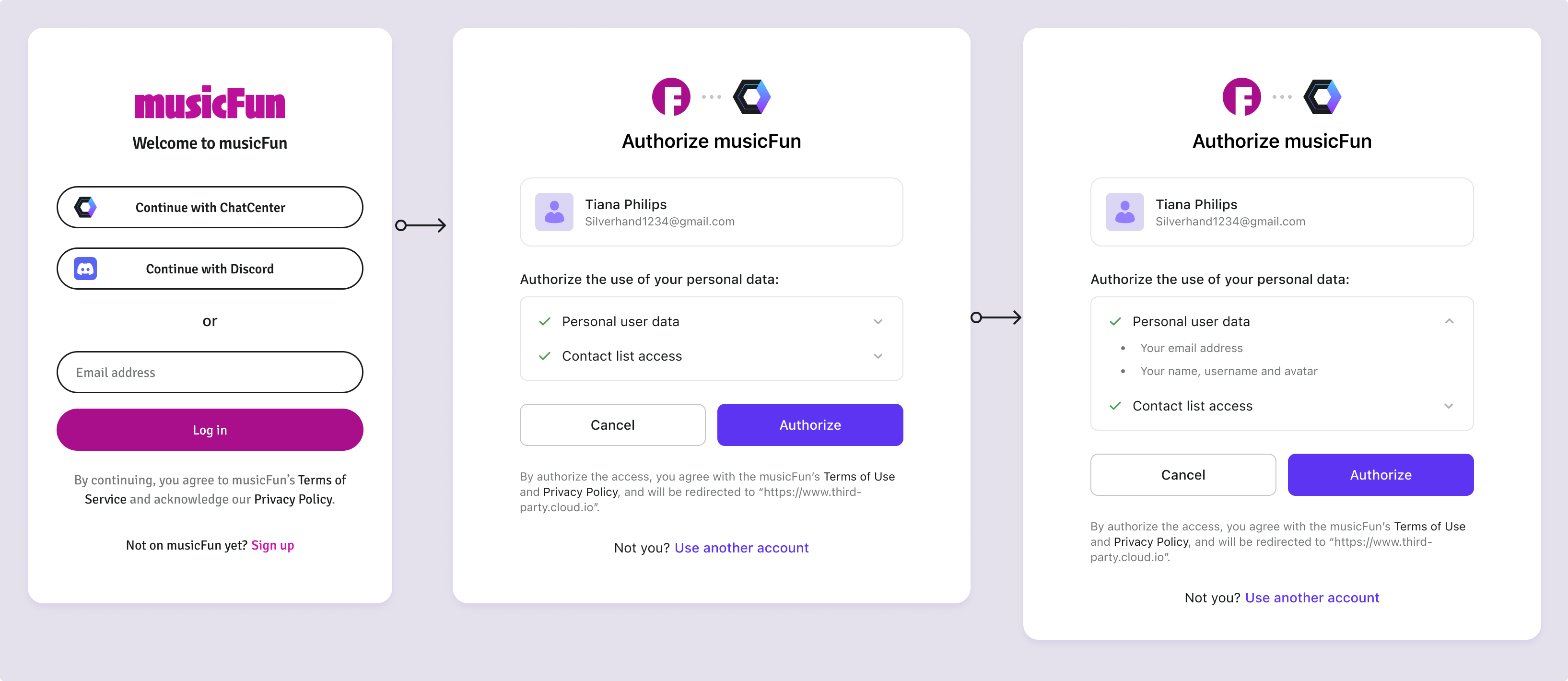
Grant permissions of user data
Assign user-level permissions, including user profile permissions (e.g., email, name, and avatar) and API resources permissions (e.g., read or write access to specific resources).
The names of the requested resources (e.g., Personal user data, API name) and specific permission descriptions (e.g., Your email address) will appear on the consent screen for users to review.
By clicking the Authorize button, users agree to grant the specified permissions to the third-party application.
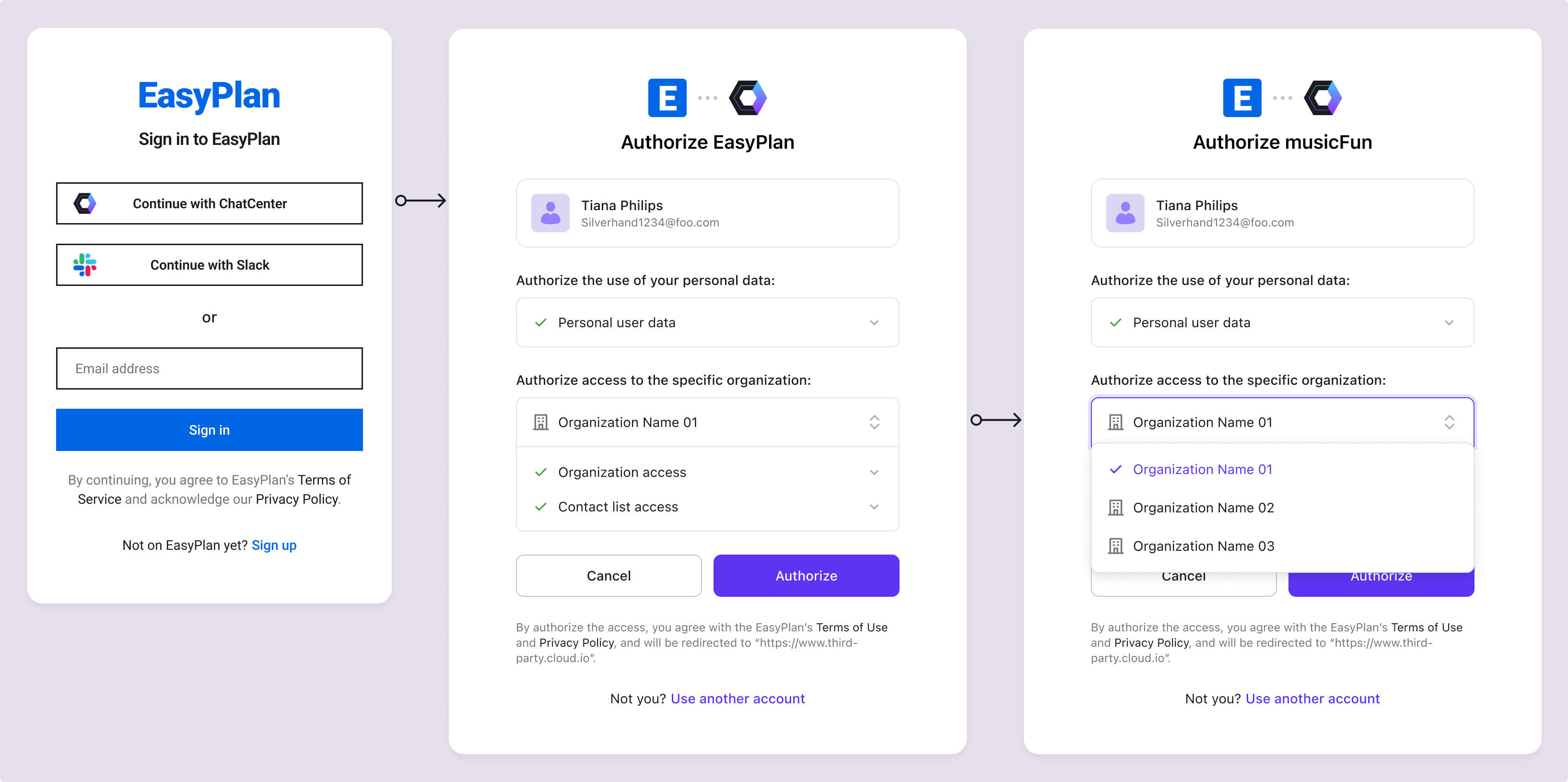
Grant permissions of organization data
Assign organization-level permissions, including organization permissions and API resources permissions. Logto allows API resources to be assigned to specific organization roles.
On the consent screen, organization data is displayed separately from user data. During the authorization flow, user must select a specific organization to grant access. Users can switch between organizations before confirming. The third-party application will only receive access to the selected organization's data and associated permissions.
Permissions types
User permissions (User profile scopes)
Those permissions are OIDC standard and Logto's essential user profile scopes used for accessing user claims. User claims will be returned in the ID token and userinfo endpoint accordingly.
profile: OIDC standard scope, used for accessing user name and avatar.email: OIDC standard scope, used for accessing user email.phone: OIDC standard scope, used for accessing user phone number.custom_data: Logto user profile scope, used for accessing user custom data.identity: Logto user profile scope, used for accessing user linked social identities information.role: Logto user profile scope, used for accessing user role information.urn:logto:scope:organizations: Logto user organization scope, used for accessing user organizations information. If enabled and requested by a third-party application, an organization selector will be displayed on the consent screen. This allows users to review and choose the organization they wish to grant access to. See organizations for more details.urn:logto:scope:organization_roles: Logto user organization scope, used for accessing user organization roles information.
Requesting a non-enabled user profile scope in the authorization request will result in an error.
API resource permissions (API resource scopes)
Logto provides role-base access control (RBAC) for API resources. API resources are the resources that are owned by your service and are protected by Logto. You may assign self-define API scopes to the third-party applications to access your API resources. Please refer to Authorization for more details.
You may create and manage your API resource scopes under the Console > API resources.
API resource scopes that are not enabled to the third-party applications will be ignored when sending an authorization request. It won't be displayed on the user consent screen and won't be granted by Logto.
Organization permissions (Organization scopes)
Organization permissions are the scopes that defined exclusively for Logto organizations. They are used for accessing organization information and resources.
In order to use Logto organization permissions, you need to enable the urn:logto:scope:organizations user scope. Otherwise the organization permissions will be ignored when sending an authorization request.
You can define your own organization scopes under the organization template settings page. Please see Organization template for more details.
Organization scopes that are not enabled to the third-party applications will be ignored when sending an authorization request. It won't be displayed on the user consent screen and won't be granted by Logto.
Default OIDC permissions
Core OIDC permissions are automatically configured for your app. These scopes are required for OIDC authentication and will not appear on the user consent screen. OAuth apps can choose not to request them if OIDC authentication isn’t needed.
-
openid: Required for OIDC authentication (optional for pure OAuth). Grants an ID token and access to theuserinfo_endpoint. -
offline_access: Optional. Retrieves refresh tokens for long-lived access or background tasks.