Logto is an Auth0 alternative designed for modern apps and SaaS products. It offers both Cloud and Open-source services to help you quickly launch your identity and management (IAM) system. Enjoy authentication, authorization, and multi-tenant management all in one.
We recommend starting with a free development tenant on Logto Cloud. This allows you to explore all the features easily.
In this article, we will go through the steps to quickly build the SendGrid sign-in experience (user authentication) with .NET Core (Blazor WebAssembly) and Logto.
Prerequisites
- A running Logto instance. Check out the introduction page to get started.
- Basic knowledge of .NET Core (Blazor WebAssembly).
- A usable SendGrid account.
Create an application in Logto
Logto is based on OpenID Connect (OIDC) authentication and OAuth 2.0 authorization. It supports federated identity management across multiple applications, commonly called Single Sign-On (SSO).
To create your Single page app application, simply follow these steps:
- Open the Logto Console. In the "Get started" section, click the "View all" link to open the application frameworks list. Alternatively, you can navigate to Logto Console > Applications, and click the "Create application" button.
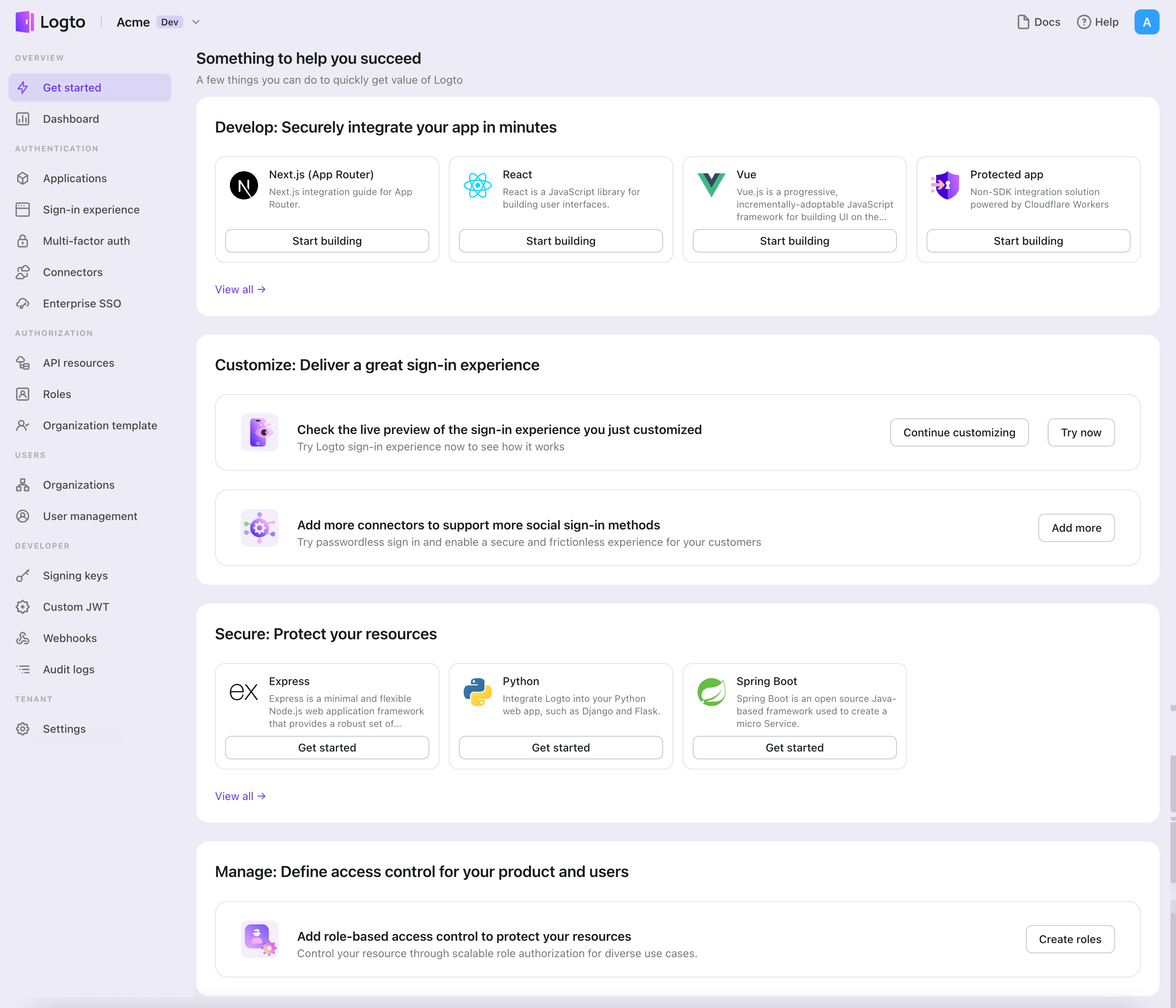
- In the opening modal, click the "Single page app" section or filter all the available "Single page app" frameworks using the quick filter checkboxes on the left. Click the ".NET Core (Blazor WebAssembly)" framework card to start creating your application.
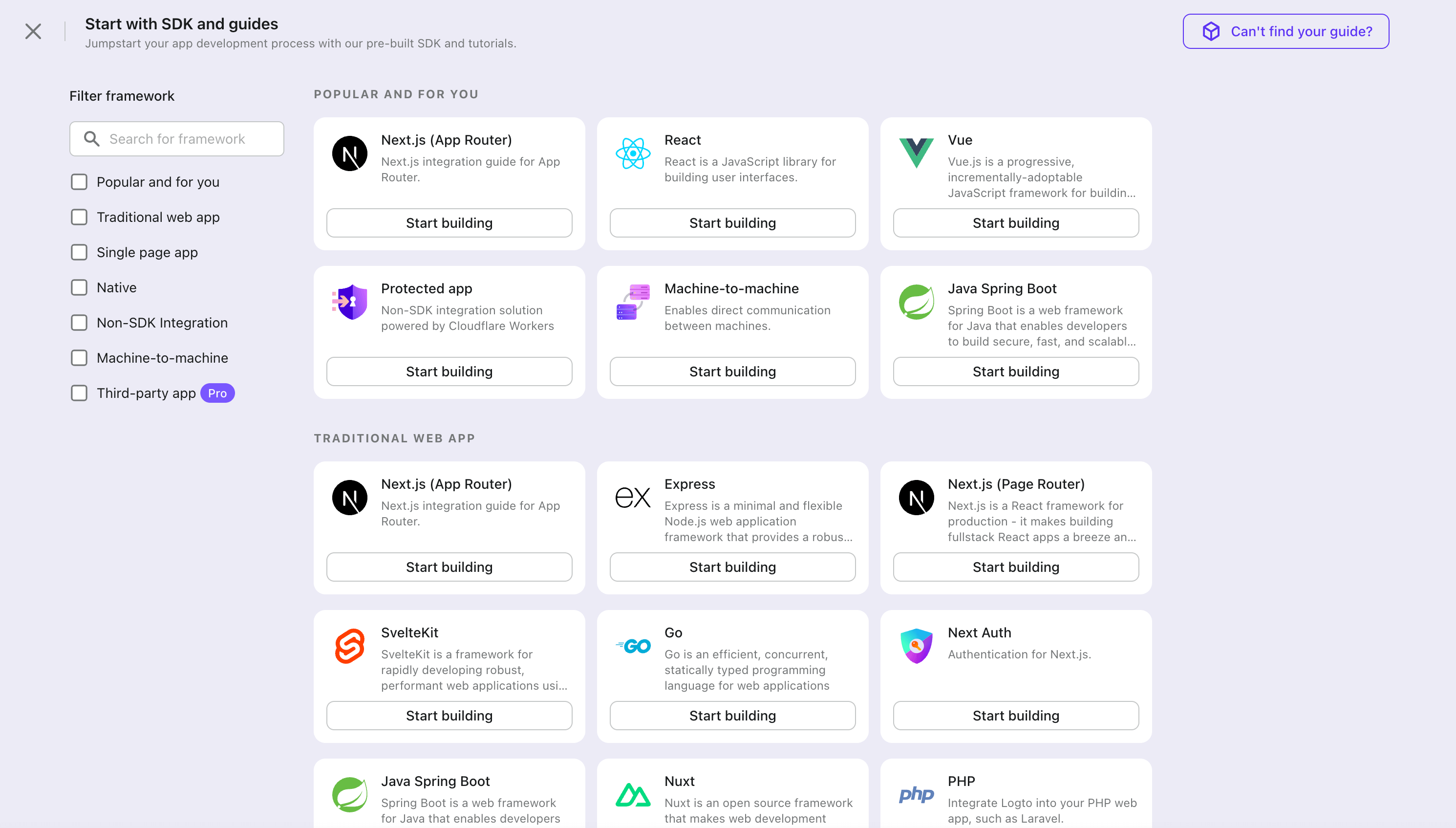
- Enter the application name, e.g., "Bookstore," and click "Create application".
🎉 Ta-da! You just created your first application in Logto. You'll see a congrats page which includes a detailed integration guide. Follow the guide to see what the experience will be in your application.
Integrate .NET Core (Blazor WebAssembly) with Logto
- The following demonstration is built on .NET Core 8.0 and Blorc.OpenIdConnect.
- The .NET Core sample projects are available in the GitHub repository.
Installation
Add the NuGet package to your project:
dotnet add package Blorc.OpenIdConnect
Add script references
Include Blorc.Core/injector.js the index.html file:
<head>
<!-- ... -->
<script src="_content/Blorc.Core/injector.js"></script>
<!-- ... -->
</head>
Register services
Add the following code to the Program.cs file:
using Blorc.OpenIdConnect;
using Blorc.Services;
builder.Services.AddBlorcCore();
builder.Services.AddAuthorizationCore();
builder.Services.AddBlorcOpenIdConnect(
options =>
{
builder.Configuration.Bind("IdentityServer", options);
});
var webAssemblyHost = builder.Build();
await webAssemblyHost
.ConfigureDocumentAsync(async documentService =>
{
await documentService.InjectBlorcCoreJsAsync();
await documentService.InjectOpenIdConnectAsync();
});
await webAssemblyHost.RunAsync();
There's no need to use the Microsoft.AspNetCore.Components.WebAssembly.Authentication package. The Blorc.OpenIdConnect package will take care of the authentication process.
Configure redirect URIs
Before we dive into the details, here's a quick overview of the end-user experience. The sign-in process can be simplified as follows:
- Your app invokes the sign-in method.
- The user is redirected to the Logto sign-in page. For native apps, the system browser is opened.
- The user signs in and is redirected back to your app (configured as the redirect URI).
Regarding redirect-based sign-in
- This authentication process follows the OpenID Connect (OIDC) protocol, and Logto enforces strict security measures to protect user sign-in.
- If you have multiple apps, you can use the same identity provider (Logto). Once the user signs in to one app, Logto will automatically complete the sign-in process when the user accesses another app.
To learn more about the rationale and benefits of redirect-based sign-in, see Logto sign-in experience explained.
In the following code snippets, we assume your app is running on http://localhost:3000/.
Configure redirect URIs
Switch to the application details page of Logto Console. Add a redirect URI http://localhost:3000/callback.

Just like signing in, users should be redirected to Logto for signing out of the shared session. Once finished, it would be great to redirect the user back to your website. For example, add http://localhost:3000/ as the post sign-out redirect URI section.
Then click "Save" to save the changes.
Configure application
Add the following code to the appsettings.json file:
{
// ...
IdentityServer: {
Authority: 'https://<your-logto-endpoint>/oidc',
ClientId: '<your-logto-app-id>',
PostLogoutRedirectUri: 'http://localhost:3000/',
RedirectUri: 'http://localhost:3000/callback',
ResponseType: 'code',
Scope: 'openid profile', // Add more scopes if needed
},
}
Remember to add the RedirectUri and PostLogoutRedirectUri to the list of allowed redirect URIs in the Logto application settings. They are both the URL of your WASM application.
Add AuthorizeView component
In the Razor pages that require authentication, add the AuthorizeView component. Let's assume it's the Home.razor page:
@using Microsoft.AspNetCore.Components.Authorization
@page "/"
<AuthorizeView>
<Authorized>
@* Signed in view *@
<button @onclick="OnLogoutButtonClickAsync">
Sign out
</button>
</Authorized>
<NotAuthorized>
@* Unauthenticated view *@
<button @onclick="OnLoginButtonClickAsync">
Sign in
</button>
</NotAuthorized>
</AuthorizeView>
Set up authentication
In the Home.razor.cs file (create it if it doesn't exist), add the following code:
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Components;
using Microsoft.AspNetCore.Components.Web;
using Blorc.OpenIdConnect;
using Microsoft.AspNetCore.Components.Authorization;
[Authorize]
public partial class Home : ComponentBase
{
[Inject]
public required IUserManager UserManager { get; set; }
public User<Profile>? User { get; set; }
[CascadingParameter]
protected Task<AuthenticationState>? AuthenticationStateTask { get; set; }
protected override async Task OnInitializedAsync()
{
User = await UserManager.GetUserAsync<User<Profile>>(AuthenticationStateTask!);
}
private async Task OnLoginButtonClickAsync(MouseEventArgs obj)
{
await UserManager.SignInRedirectAsync();
}
private async Task OnLogoutButtonClickAsync(MouseEventArgs obj)
{
await UserManager.SignOutRedirectAsync();
}
}
Once the user is authenticated, the User property will be populated with the user information.
Checkpoint: Test your application
Now, you can test your application:
- Run your application, you will see the sign-in button.
- Click the sign-in button, the SDK will init the sign-in process and redirect you to the Logto sign-in page.
- After you signed in, you will be redirected back to your application and see the sign-out button.
- Click the sign-out button to clear token storage and sign out.
Add SendGrid connector
Email connector is a method used to send one-time passwords (OTPs) for authentication. It enables Email address verification to support passwordless authentication, including Email-based registration, sign-in, two-factor authentication (2FA), and account recovery. You can easily connect SendGrid as your Email provider. With the Logto Email connector, you can set this up in just a few minutes.
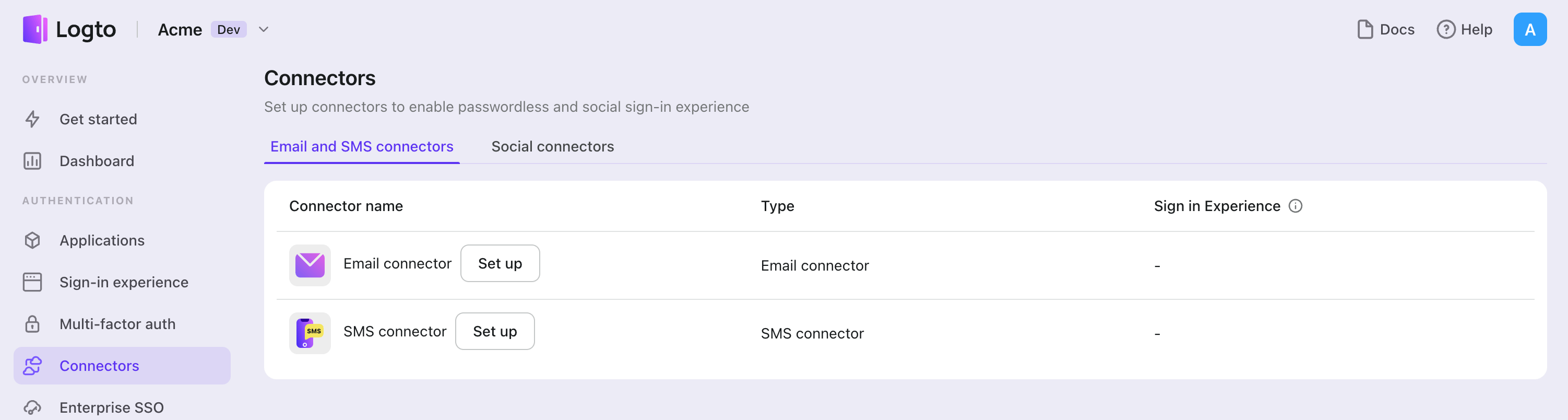
To add a Email connector, simply follow these steps:
- Navigate to Console > Connector > Email and SMS connectors.
- To add a new Email connector, click the "Set up" button and select "SendGrid".
- Review the README documentation for your selected provider.
- Complete the configuration fields in the "Parameter Configuration" section.
- Customize the Email template using the JSON editor.
- Test your configuration by sending a verification code to your Email address.
If you are following the in-place Connector guide, you can skip the next section.
Set up SendGrid email connector
Register SendGrid account
Create a new account at SendGrid website. You may skip this step if you've already got an account.
Verify senders
Go to the SendGrid console page and sign in with your SendGrid account.
Senders indicate the addresses our verification code email will be sent from. In order to send emails via the SendGrid mail server, you need to verify at least one sender.
Starting from the SendGrid console page, go to "Settings" -> "Sender Authentication" from the sidebar.
Domain Authentication is recommended but not obligatory. You can click "Get started" in "Authenticate Your Domain" card and follow the upcoming guide to link and verify a sender to SendGrid.
By clicking the "Verify a Single Sender" button in the panel, you are now focusing on a form requiring some critical information to create a sender. Follow the guide, fill out all these fields, and hit the "Create" button.
After the single sender is created, an email with a verification link should be sent to your sender's email address. Go to your mailbox, find the verification mail and finish verifying the single sender by clicking the link given in the email. You can now send emails via SendGrid connector using the sender you've just verified.
Create API keys
Let's start from the SendGrid console page, go to "Settings" -> "API Keys" from the sidebar.
Click the "Create API Key" in the top-right corner of the API Keys page. Type in the name of the API key and customize "API Key Permission" per your use case. A global Full Access or Restricted Access with full access to Mail Send is required before sending emails with this API key.
The API Key is presented to you on the screen as soon as you finished the Create API Key process. You should save this API Key somewhere safe because this is the only chance that you can see it.
Configure your connector
Fill out the apiKey field with the API Key created in "Create API keys" section.
Fill out the fromEmail and fromName fields with the senders' From Address and Nickname. You can find the sender's details on the "Sender Management" page. fromName is OPTIONAL, so you can skip filling it.
You can add multiple SendGrid mail connector templates for different cases. Here is an example of adding a single template:
- Fill out the
subjectfield, which works as the title of emails. - Fill out the
contentfield with arbitrary string-typed contents. Do not forget to leave the{{code}}placeholder for the random verification code. - Fill out
usageTypefield with eitherRegister,SignIn,ForgotPassword,Genericfor different use cases. - Fill out
typefield with eithertext/plainortext/htmlfor different types of content.
In order to enable full user flows, templates with usageType Register, SignIn, ForgotPassword and Generic are required.
Here is an example of SendGrid connector template JSON.
[
{
"subject": "<register-template-subject>",
"content": "<Logto: Your verification code is {{code}}. (register template)>",
"usageType": "Register",
"type": "text/plain",
},
{
"subject": "<sign-in-template-subject>",
"content": "<Logto: Your verification code is {{code}}. (sign-in template)>",
"usageType": "SignIn",
"type": "text/plain",
},
{
"subject": "<forgot-password-template-subject>",
"content": "<Logto: Your verification code is {{code}}. (forgot-password template)>",
"usageType": "ForgotPassword",
"type": "text/plain",
},
{
"subject": "<generic-template-subject>",
"content": "<Logto: Your verification code is {{code}}. (generic template)>",
"usageType": "Generic",
"type": "text/plain",
},
]
Test SendGrid email connector
You can type in an email address and click on "Send" to see whether the settings can work before "Save and Done".
That's it. Don't forget to Enable connector in sign-in experience
Config types
| Name | Type |
|---|---|
| apiKey | string |
| fromEmail | string |
| fromName | string (OPTIONAL) |
| templates | Template[] |
| Template Properties | Type | Enum values |
|---|---|---|
| subject | string | N/A |
| content | string | N/A |
| usageType | enum string | 'Register' | 'SignIn' | 'ForgotPassword' | 'Generic' |
| type | enum string | 'text/plain' | 'text/html' |
Save your configuration
Double check you have filled out necessary values in the Logto connector configuration area. Click "Save and Done" (or "Save changes") and the SendGrid connector should be available now.
Enable SendGrid connector in Sign-in Experience
Once you create a connector successfully, you can enable phone number-based passwordless login and registration.
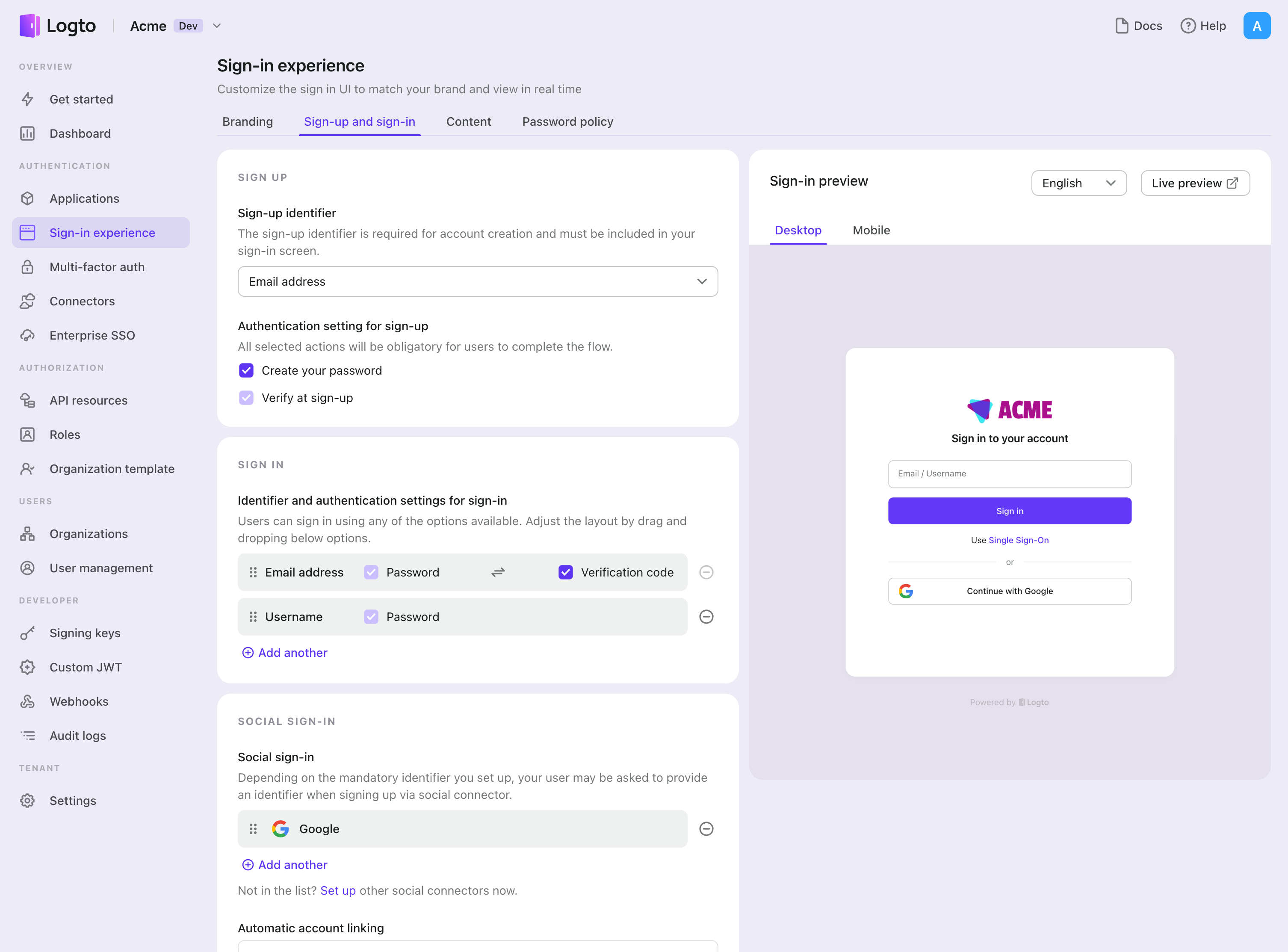
- Navigate to Console > Sign-in experience > Sign-up and sign-in.
- Set up sign-up methods (Optional):
- Select "Email address" or "Email or phone number" as the sign-up identifier.
- "Verify at sign-up" is forced to be enabled. You can also enable "Create a password" on registration.
- Set up sign-in methods:
- Select Email address as one of sign-in identifiers. You can provide multiple available identifiers (email, phone number, and username).
- Select "Verification code" and / or "Password" as the authentication factor.
- Click "Save changes" and test it in "Live preview".
In addition to registration and login via OTPs, you can also have password recovery and -based security verification enabled, as well as linking Email address to profile. See End-user flows for more details.
Testing and Validation
Return to your .NET Core (Blazor WebAssembly) app. You should now be able to sign in with SendGrid. Enjoy!
Further readings
End-user flows: Logto provides a out-of-the-box authentication flows including MFA and enterprise SSO, along with powerful APIs for flexible implementation of account settings, security verification, and multi-tenant experience.
Authorization: Authorization defines the actions a user can do or resources they can access after being authenticated. Explore how to protect your API for native and single-page applications and implement Role-based Access Control (RBAC).
Organizations: Particularly effective in multi-tenant SaaS and B2B apps, the organization feature enable tenant creation, member management, organization-level RBAC, and just-in-time-provisioning.
Customer IAM series Our serial blog posts about Customer (or Consumer) Identity and Access Management, from 101 to advanced topics and beyond.